One Appliance – One Image is what Cisco is targeting for its Next Generation Firewalls. With this vision, Cisco has created a unified software image named “Cisco Firepower Threat Defense”. In this FirePOWER series article we’ll cover the installation of Firepower Threat Defense (FTD) on a Cisco ASA 5500-X series security appliance. We’ll also explain the management options available: Firepower Management Center (FMC) which is the old FireSIGHT and Firepower Device Manager (FDM).
Cisco Firepower Threat Defense (FTD) is a unified software image, which is a combination of Cisco ASA and Cisco FirePOWER services features that can be deployed on Cisco Firepower 4100 and the Firepower 9300 Series appliances as well as on the ASA 5506-X,ASA 5506H-X, ASA 5506W-X, ASA 5508-X, ASA 5512-X, ASA 5515-X, ASA 5516-X, ASA 5525-X, ASA 5545-X, and ASA 5555-X. However, at the time of writing, the Cisco Firepower Threat Defense (FTD) unified software cannot be deployed on Cisco ASA 5505 and 5585-X Series appliances.
Understanding Cisco Firepower Threat Defense Management & Capabilities
Simplifying management and operation of Cisco’s Next Generation Firewalls is one of the primary reasons Cisco is moving to a unified image across its firewall appliances.
Currently the Firepower Threat Defense can be managed through the Firepower Device Management (similar to Cisco’s ASDM) and Firepower Management Center (analyzed below).
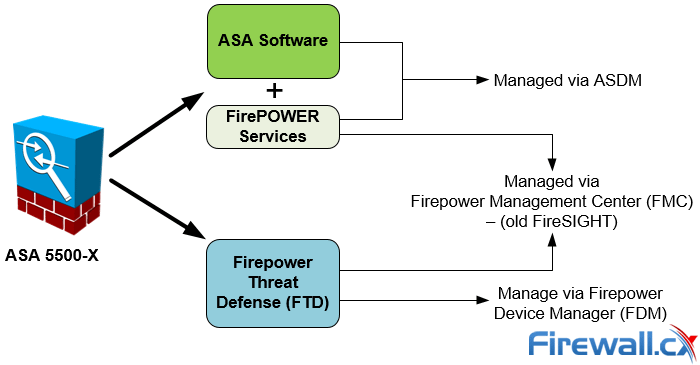
Managing Options for FirePOWER Services and Firepower Threat Defense (FTD)
It should be noted that the Firepower Device Management software is under extensive development and is not currently capable of supporting all configuration options. For this reason it’s best to rely on the Firepower Management Center to manage the Cisco Firepower Threat Defense system.
The Firepower Management Center, also known as FMC or FireSIGHT, is available as a dedicated server or virtual image appliance (Linux based VM server) that connects to the FirePOWER or Firepower Threat Defense and allows you to fully manage either system. Organizations with multiple Firepower Threat Defense systems or FirePOWER Services would register and manage them from the FMC.
Alternatively, users can manage the Firepower Threat Defense (FTD) device using the Firepower Device Manager (FDM) – the concept is similar to ASDM.
Currently the latestCisco Firepower Threat Defense (FTD) unified software image available is version 6.2.x .
The Cisco Firepower Threat Defense is continually expanding the Next-Generation Firewall Servicesit supports which currently includes:
- Stateful Firewall Capabilities
- Static and Dynamic Routing. Supports RIP, OSPF, BGP, Static Routing
- Next-Generation Intrusion Prevention Systems (NGIPS)
- URL Filtering
- Application Visibility and Control (AVC)
- Advance Malware Protection (AMP)
- Cisco Identity Service Engine (Cisco ISE) Integration
- SSL Decryption
- Captive Portal (Guest Web Portal)
- Multi-Domain Management
- Rate Limiting
- Tunnelled Traffic Policies
- Site-to-Site VPN. Only supports Site-to-Site VPN between FTD appliances and FTD to ASA
- Multicast Routing Shared NAT
- Limited Configuration Migration (ASA to Firepower TD)
While the Cisco Firepower Threat Defense is being actively developed and populated with some great features, we feel that it’s too early to place it in a production environment. There are some stability issues, at least with the FTD image on the ASA platform, which should be ironed out with the newer software releases.
If you are already in the process of installing FTD on your ASA then you should heavily test it before rolling it out to production.
Due to the issues encountered, we were forced to remove the FTD installation by reimaging our ASA 5555-X Appliance with Cisco ASA and FirePOWER Services images. We believe the “Cisco Firepower Threat Defense” unified software image is very promising but requires some more time to reach a more mature and stable version.
Reimaging the Cisco ASA 5555-X Appliance to install the Cisco Firepower Threat Defense image is fairly simple once you understand what needs to be done. Here are the steps in the order they must be executed: